Best known practices for using OpenSSH
As the name suggests, OpenSSH is an Open-source client and server application of SSH (Secure Shell) protocol used by almost every Linux and Unix Distributions. It’s a network traffic encryption tool mainly used by network administrators to gain access to remote *nix and *BSD servers. This application encrypts any data transferred through and from SSH protocol, therefor it’s effective against all sorts of possible attacks like sniffing, session hi-jacking, etc.
How to Secure OpenSSH ?
These are the seven necessary security measurements that can be taken to ensure security of your SSH server setup:
- It requires a strong password.
- Change default port for SSH connectivity.
- Protocol version 2 should be used.
- Login from user root should be restricted.
- Limiting the user access.
- Use key-based for authentication instead of a password.
It requires a strong password
An Example of a strong password varies. It could contain combination of alpha numbers and special characters (such as @,;/&) or it could even contain ASII codes like (ß æ ê etc). One thing to keep in mind is that you should never use easy to guess passwords such as admin2015 or admin1234 or root786. Example of a strong password can be /H3lL0w.@RD/ (slashes are also part of the password).
Change default port for SSH connectivity
The default port for SSH is TCP port 22. So, changing the default port will not only dodge the attacker but it also reduces potentially huge amount of traffic that attacker may impose on your server through brute force attack as port 22 is a common target port used for SSH brute force attack.
In order to change the default port, you will have to edit the config file “sshd_config” located in folder /etc/ssh/.
Use the command below to edit this file.
nano /etc/ssh/sshd_config
Press Ctrl+W to search for the string “port”
port 22
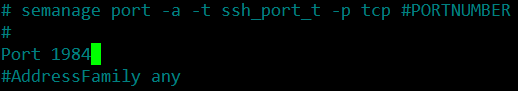
Once found, change it to any desirable port number, for instance 1984.
port 1984
Note: Make sure the port you’re using is not already in use by the server. The command below should reveal if our desired port is free or not (if the result returns nothing, then it means the port is free to use)
netstat -ntap | grep 1984
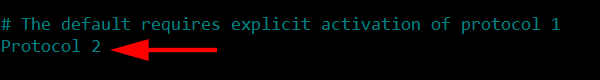
Protocol version 2 should be used
In order to achieve this goal we will continue editing the same /etc/ssh/sshd_config file. SSH can be configured to use two of the available protocol version and it’s recommended to use protocol version 2 which is more secure and encrypted.
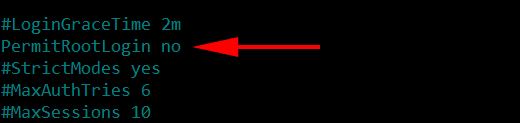
Login from user root should be restricted
It is advised to disable the direct login from the user root as it may allow the attacker to directly brute force the root privileges which will give full administrative access to the attacker if success is achieved. But, before you disable your root login you should make sure that there is another alternate user name available to gain access to your SSH server.
Limiting the user access
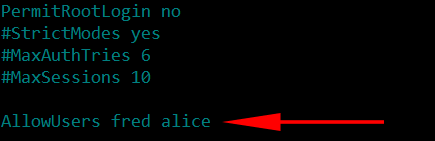
After disabling the root account for SSH, you should limit the number of users that can access the server. There maybe more than 2 and possibly more than 100 users on a server and definitely not all users should be allowed to access the SSH. Therefor choosing selected users will ensure further security. For instance there are two users you want to allow fred and alice the code to achieve this goal would be:
AllowUsers fred alice
Use key-based for authentication instead of a password
Since there’s always a chance for a brute force attack or the password some how being leaked or guessed, it is advisable to disable user access to SSH using password. Alternate method for accessing the SSH would be encrypted Key-based authentication.
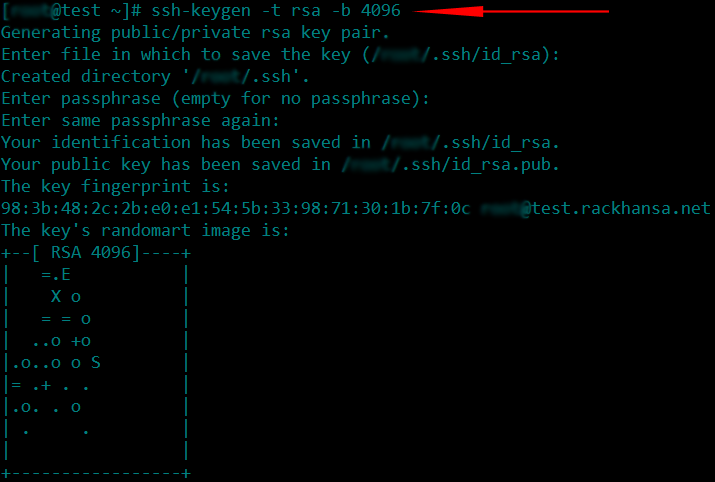
In order to achieve this goal we are required to create a public/private key using the following command:
This will create 2 files in the directory ~/.ssh/ a file name by id_rsa which is the private key and id_rsa.pub would be the public.key. Public key id_rsa.pub should be uploaded to your server by using the following command:
ssh-copy-id -i ~/.ssh/id_rsa.pub serverusername@serveripaddress
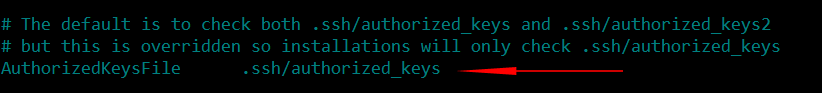
This will write a public key to the file ~/.ssh/authorized_keys director on your server.
After this has been accomplished, you can go back to the ssh configuration file and uncomment the following line:
Final steps would be restarting the sshd service and reconnecting to your SSH using the new port number.
systemctl restart sshd ssh -p 1984 username@serverIPaddress